Pages

Cryptography
is failing.

Today, digital Information is secured and verified using cryptography built on math problems considered unbreakable by regular computers.


For quantum computers, these same math problems are trivial – allowing them to easily break today’s strongest encryption.
The problems
we're addressing.
.svg)
Visibility
Cryptography is buried everywhere inside technology. Standard security tools typically lack the ability to help businesses understand where it is & how it's used.
.svg)
"Q-Day"
Advancements in quantum computing & the standardization of quantum-safe cryptography have accelerated the requirement to overhaul PKI.
.svg)
Intrusion & Interoperability
Detection of cryptography can be intrusive if not managed correctly. Organizations require systematic discovery & remediations without downtime.
Introducing QuantumShield™
Discover
Automating the inventory of IT & cryptographic assets for a non-invasive posture report.
Assess
Inventory + business context = risk & dependency analysis in your language.
Protect
Immediate defense model secures systems and data today without requiring complex code refactoring.
Monitor
Continuous monitoring provides validation of data protection for internal & external stakeholders.
Protection That
Starts Now
Immediate Insights
We provide customizable dashboarding to surface visuals for the data you need to build the reports you want.
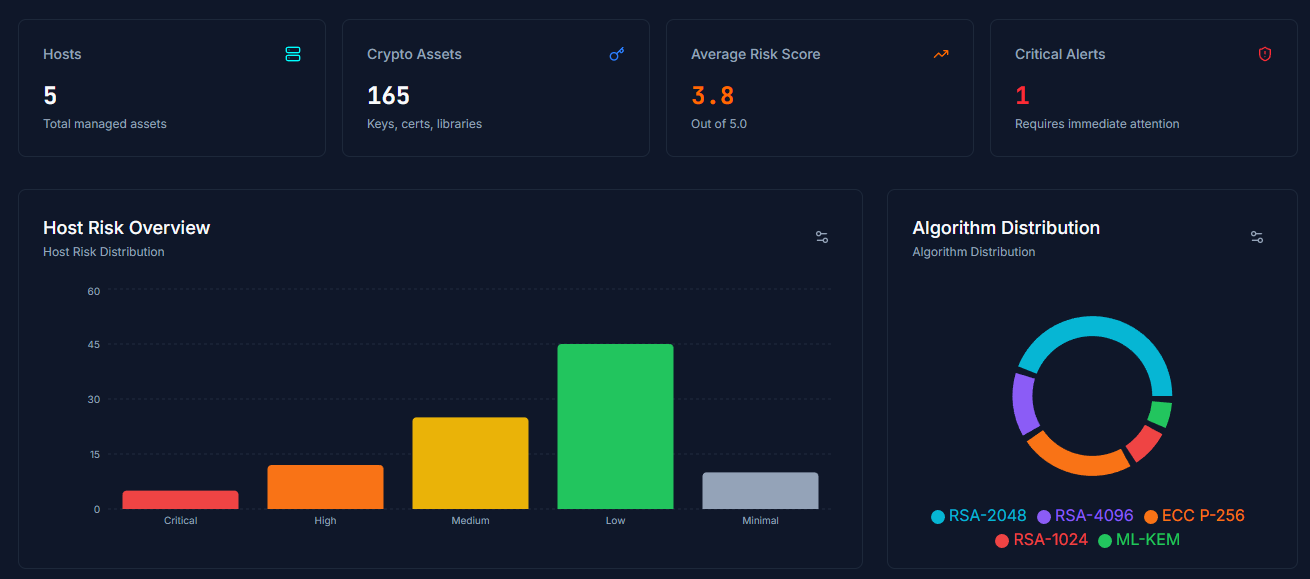
Data Collection
Seamless Integrations with industry-standard vendors allow for low friction onboarding and insight production that takes days, not weeks.
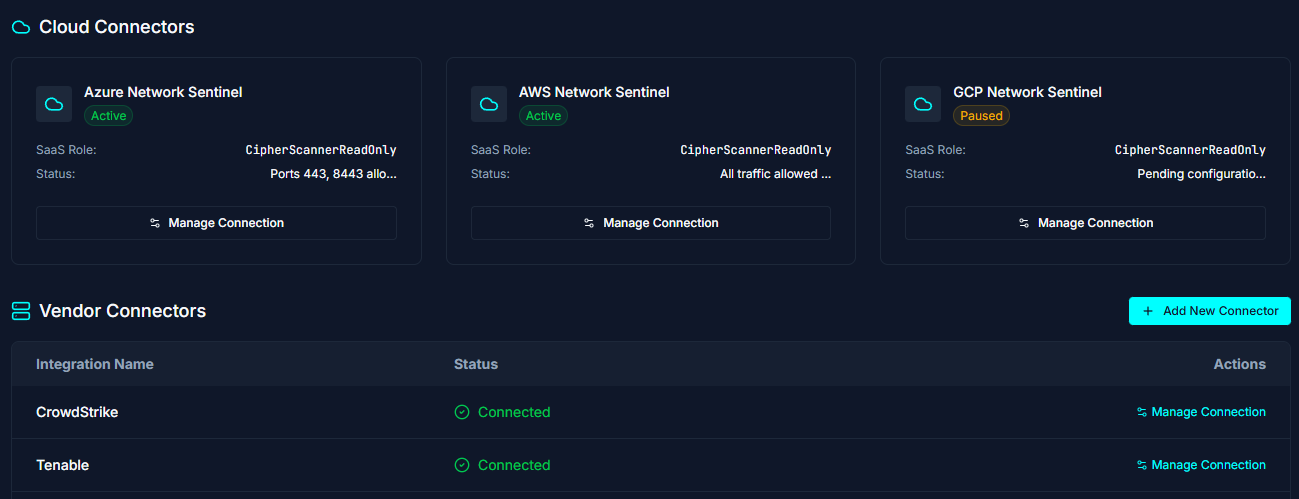
.png)
Securing the Future of
Enterprise Encryption
Built for the next era of encryption, enabling enterprises to secure data, demonstrate compliance, and move confidently into post-quantum security.
.svg)
Full Visibility
See every cryptographic asset and vulnerability.
.svg)
Automated Discovery
Expose hidden cryptographic assets and outdated protocols.
.svg)
Prioritized Action
Rank vulnerabilities and business impact with AI-driven risk analysis.
.svg)
Seamless Migration
Orchestrate & validate immediate post-quantum readiness.
.svg)
Continuous Compliance
Prove state-of-the-art protection to regulators & data owners.
.svg)
Trusted Insight
Turn business requirements into shipped protection.
.svg)
.svg)

