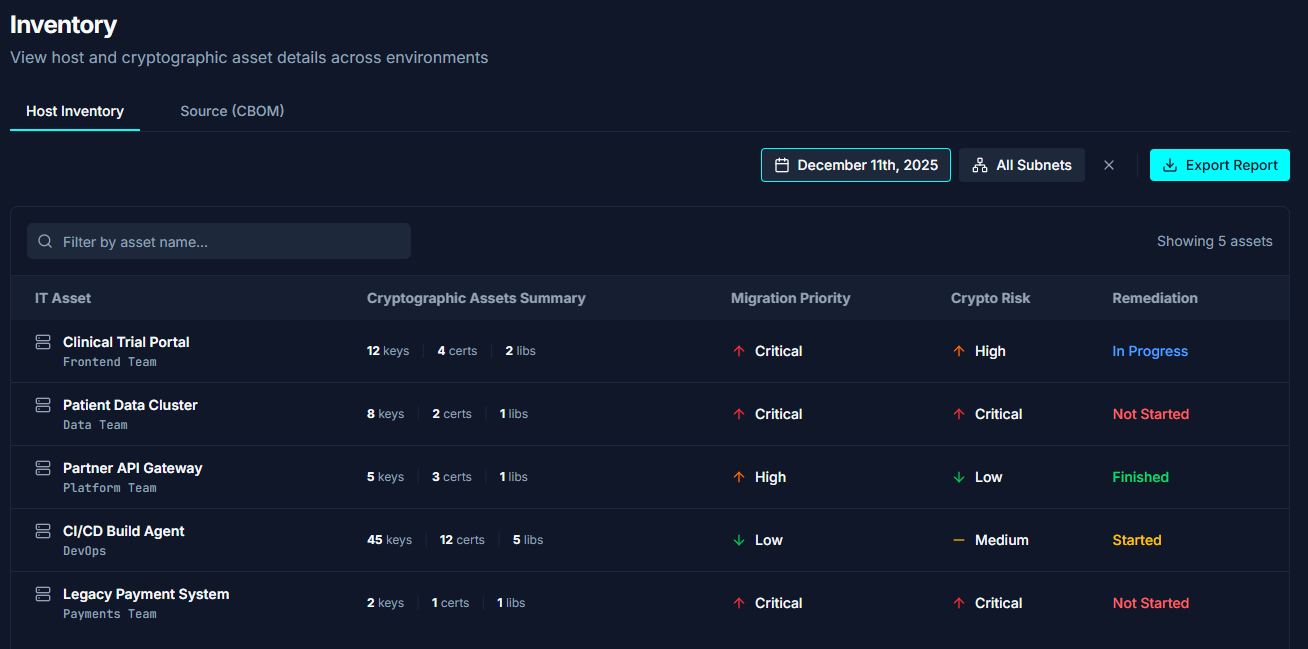
Assess Risk & Readiness
AI-powered quantum security management with data-driven prioritization.
Analyze cryptographic dependencies, rank vulnerabilities by business impact, and build a roadmap that simplifies remediataions,
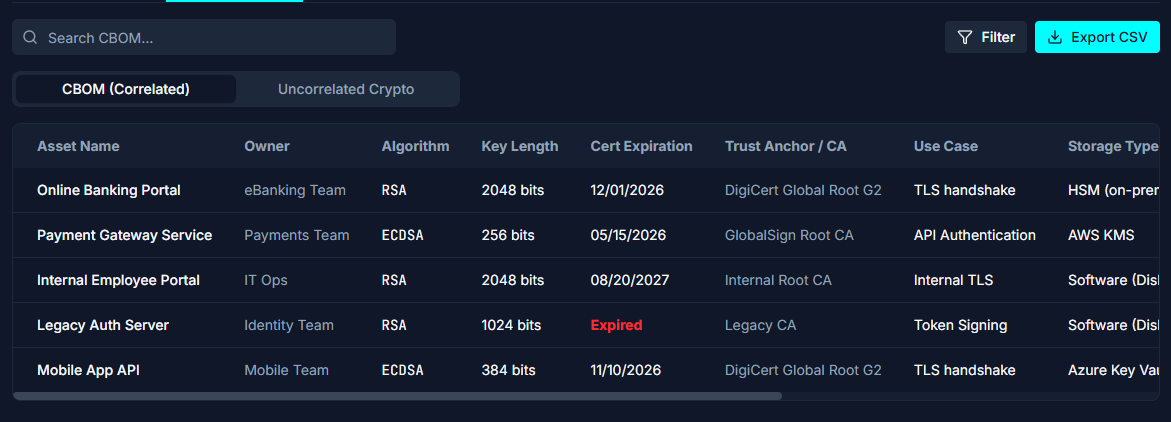
Test & Deploy
Secure data instantly with IaC protection that integrates into existing systems without disrupting performance.
Use containerized test environments for precise policy enforcement and orchestrate seamless rollout through existing CI/CD pipelines.
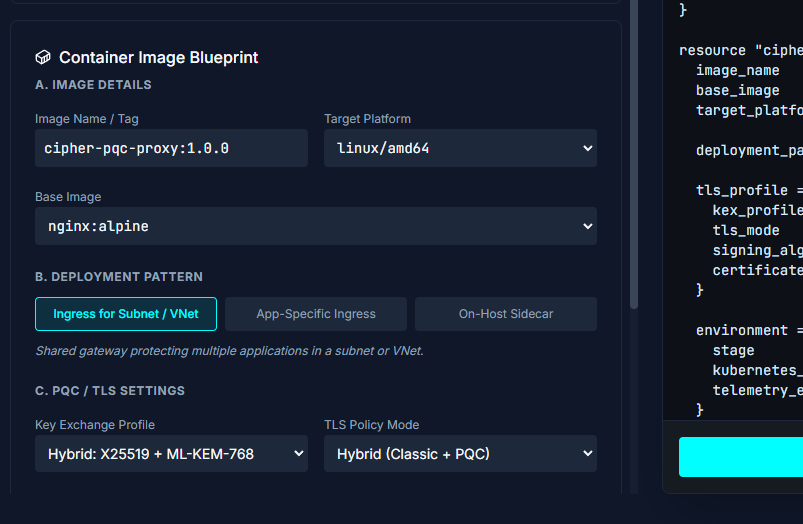
Monitoring & Reporting
Maintain continuous visibility with real-time telemetry that tracks cryptographic posture, detects drift, and delivers exportable compliance reports aligned with global PQC standards.


Explore Our
AI Capabilities
Our cutting-edge AI solutions help businesses work smarter, move faster, and protect better.
Discover & Diagnose
We begin by integrating with your ITSMs, CMDBs, cloud environments, and existing security solutions to automatically discover all cryptographic assets across hosts. Network and binary-level scans generate a complete CBOM, exposing hidden risks and dependencies.
Assess & Prioritize
Our proprietary AI engine analyzes this inventory to surface critical vulnerabilities, rank them by exposure and business impact, and outlines the most efficient remediation paths. High-risk dependencies are triaged for immediate protection while longer-term migration plans are defined.
Implement & Shield
Using IaC & ticketing workflow automations, we help teams instantly secure data without disrupting operations. This provides immediate protection while orchestration guides internal teams through safe protocol upgrades and algorithm replacements.
Test & Validate
We help teams deploy containerized test environments that mirror production to validate cryptographic updates before rollout. Continuous validation confirms performance, compatibility, and compliance with PQC guidelines and best practices.
Monitor & Maintain
Once live, centralized telemetry tracks cryptographic drift, expired certificates, and new risks. Automated compliance reporting delivers audit-ready proof aligned with evolving PQC standards, ensuring your organization stays protected and ready for future migrations.
.svg)
.svg)